Heksagon Call Validation Solution
Verify call legitimacy in real time to protect revenue, customers, and network integrity from spoofing, bypass, and flash call abuse.

Take Advantage of Real-Time Call Authentication
Call Validation is a core module within Heksagon’s Voice Firewall (VFW) suite, designed to combat increasingly sophisticated fraud scenarios like CLI spoofing, SIMBOX bypass, flash calls, and robo calls.
Heksagon Call Validation Features
By validating call legitimacy, routing consistency, and subscriber status before call setup, you can instantly block or reroute suspicious traffic and preserve interconnect margins and customer trust. We help you retain full control over your traffic and call registry, with the flexibility to define custom validation rules and exceptions. The system ensures reliable verification even in complex scenarios like non-CAMEL roaming, while maintaining a distributed architecture that eliminates single points of failure. Only minimal, hashed data is exchanged between operators, with no transfer of CDR-level information or subscriber details. This ensures compliance with data protection standards and preserves operational autonomy.
Carrier-to-carrier communication enables high-volume validation without central bottlenecks. You can connect directly or via a regional hub, with onboarding streamlined through a central authentication service. Public API specifications for HTTP and CAMEL make integration fast and future-proof, while open interworking ensures compatibility with your other validation platforms.
End-to-End Call Validation
- Out-of-band verification using hashed call data (MD5 of CLI + called number).
- Origin validation: confirms if CLI was registered in the originating network.
- Termination validation: uses temporary routing numbers to protect the call path.
Regional Call Validation
- Protects operators within a region from spoofed CLI using local numeration.
- Uses open SRI-4-SM over SS7 or HTTP API for roaming status checks.
Real-Time Number Verification
- Real-time roaming status checks via SS7 MAP or HTTP API.
- Detection of “impossible” traffic (e.g. national CLI from international routes).
- Lightweight implementation suitable for regional MNO cooperation.
Call Signature Control
- Supports STIR/SHAKEN and other signature verification methods.
- Prevents spoofing and impersonation attacks.
Social Engineering & Fraud Prevention
- Alerts for suspicious calls to/from known fraud numbers.
- Validation of bank call center traffic to prevent spoofed calls.
- Integration with commercial organizations for branded calling and verification.
- Addresses CLI spoofing, international bypass, social engineering, spam calls, and robocalls.
Flexible Integration
- SIP, INAP/CAMEL, and SIGTRAN interfaces.
- Compatible with VoIP and TDM networks.
- API support for HTTP/REST and SOAP/XML.
How Heksagon Call Validation Works
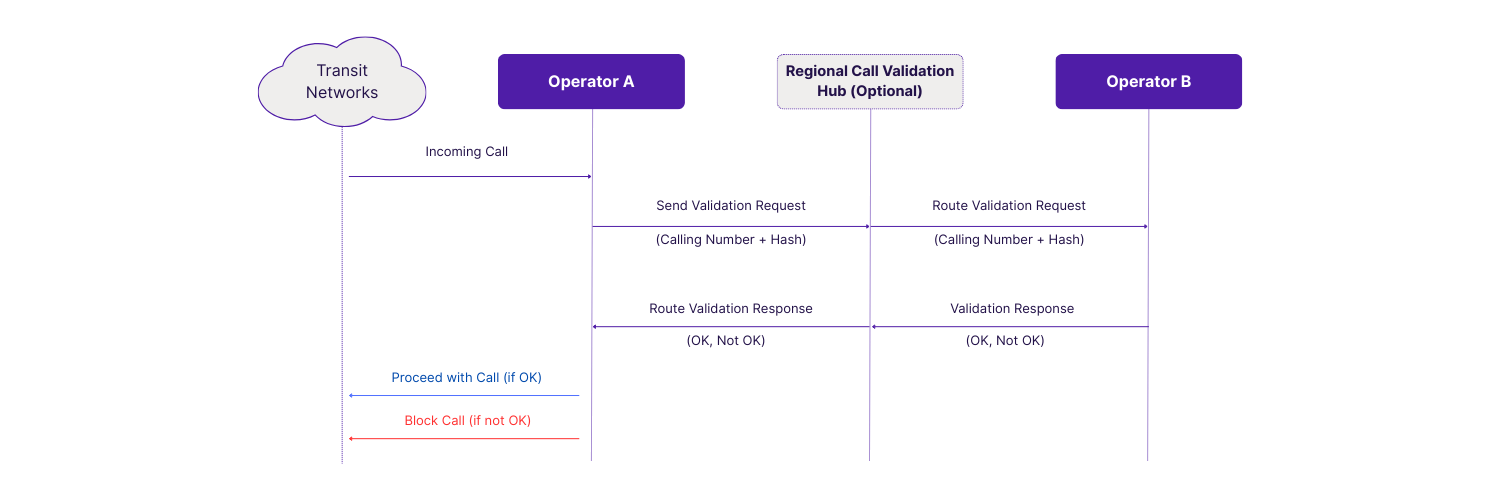
Validation Logic
When Operator A receives a call with a CLI that belongs to Operator B, the system initiates a validation process to answer key questions:
- Did the call actually originate in Operator B’s network?
- Is the subscriber (calling party) in a valid state to initiate calls?
- Is the subscriber roaming in a way that prevents real-time tracking (e.g., non-CAMEL roaming)?
Based on the response, Operator A can decide whether to allow, block, reroute, or suppress the call.
Validation Methods
Heksagon supports multiple validation mechanisms, depending on the network environment and regulatory context:
Subscriber Status Validation
- Uses SS7 MAP or HTTP API to query the home operator about the subscriber’s current status.
- Can bypass limitations like SRI4SM home-zone protection or ATI restrictions for trusted partners.
Call Status Validation
- Verifies whether a specific call is active in the originating network.
- Uses API calls to check the call registry of the partner operator.
Interworking Architecture
- Bilateral Model: Operators connect directly to each other for validation.
- Hub Model: Operators connect to a centralized traffic control hub, simplifying routing and scaling.
Privacy & Security
- Validation requests use hashed identifiers (e.g., MD5 of CLI + called number) to protect sensitive data.
- No full call details or subscriber information are exchanged.
- Operators retain control over their own call registries and validation logic.
Heksagon Call Validation Resources
-
Call Validation Product Brief
Need more information on our Call Validation solution? Take a look at our latest Product Brief!
Related Products
Didn't Find What You Were Looking For?
Frequently Asked Questions
What is Call Validation and why is it critical for telecom operators?
Call Validation is a real-time process that verifies whether an incoming call is legitimate. It checks if the calling number is active in the originating network and if the subscriber is authorized to make calls. It helps prevent CLI spoofing, interconnect bypass, and social engineering fraud.
How does Heksagon’s Call Validation differ from STIR/SHAKEN or other frameworks?
Our solution supports both in-band and out-of-band validation, including SS7 CAMEL and HTTP API interworking. Unlike STIR/SHAKEN, it’s optimized for regional and bilateral deployments, supports hashed call data for privacy, and doesn’t require full IP network migration.
Can Heksagon Call Validation be deployed without disrupting existing call flows?
Yes. The solution integrates seamlessly with existing core network elements (MSC, GMSC, SIP proxies) and operates independently of the call path. It uses lightweight APIs and signaling protocols to validate calls without altering routing logic.
What types of fraud does Heksagon Call Validation help prevent?
It prevents CLI spoofing, SIMBOX fraud, international bypass, robocalls, vishing, redirected calls, and impersonation attacks. especially those targeting banks and commercial call centers.
Is subscriber data exposed during the validation process?
Absolutely not. We use hashed call identifiers and optional encryption keys to ensure that no sensitive subscriber data is exchanged. Operators retain full control over their call registries and validation logic.
Can Heksagon Call Validation be used as a commercial service for banks or enterprises?
Absolutely. The Call Validation module integrates with our Branded Calling, High-Risk Call Alerts, and other B2B Services, making it ideal for financial institutions, government agencies, and regulated industries.
Let's Get in Touch!
Interested in our Call Validation Solution? Fill out the form and our solution experts will contact you in two business days!
