Heksagon Advanced SMS Firewall Solution
Secure your messaging ecosystem and maximize A2P revenues with real-time SMS fraud detection, grey route blocking, and comprehensive subscriber protection.

Secure Your Messaging Ecosystem. Maximize A2P Revenues.
Mobile operators lose billions annually to SMS grey routes and fraud. Fraudsters exploit P2P routes to deliver commercial A2P messages without authorization, bypassing your monetization systems and exposing subscribers to smishing, spam, and malicious content.
Traditional SMS management approaches cannot address the sophistication of modern messaging fraud. Grey route operators continuously evolve bypass techniques, SIMBOX operations scale rapidly, and content-based threats like smishing and malware distribution proliferate across networks.
Heksagon SMS Firewall delivers comprehensive messaging security through real-time traffic analysis, intelligent content filtering, and AI-powered fraud detection. Operating in both MAP (SS7) and SMPP protocol environments, our solution identifies unauthorized A2P traffic, blocks malicious content, and enables full monetization of your legitimate messaging ecosystem, protecting both revenues and subscribers.
Heksagon SMS Firewall Features
Built on carrier-grade architecture, Heksagon SMS Firewall operates as a real-time monitoring and control system for all SMS traffic entering your network. The solution processes messages through MAP (SIGTRAN) and SMPP interfaces, evaluating each message against configurable detection scenarios before delivery.
Real-Time Traffic Screening
- Protocol support: Full MAP (SRI4SM, FSM, delivery reports), CAMEL (SMS IDP), SIP (SMS over IP), and SMPP integration
- Dual Operation Modes: Active proxy mode for real-time blocking or passive monitoring for analytics without traffic impact
- HLR Integration: Real-time MSC/VLR queries for subscriber validation.
- Low Latency Processing: Sub-second message analysis ensures minimal impact on QoS.
- Scalability: Support for millions of messages daily with N+1 architecture
Advanced Grey Route Detection
- P2P vs A2P Classification: Real-time distinction between personal and application-originated messages
- SIMBOX Detection: Behavioral, volume, and time-of-day analysis identifying unauthorized termination devices
- Message Origination Profiling: Identifies anomalies in routing and sender behavior.
Content-Based Threat Prevention
- Smishing & Phishing Protection: URL pattern recognition and sender ID verification.
- Spam & Malware Filtering: Keyword detection, content hashing, and payload analysis.
- Flooding & Spoofing Mitigation: Threshold-based detection and origin verification.
Intelligent Rule Engine
- Dynamic Scenario Management: User-defined rules adapt to evolving fraud patterns.
- AI-Driven Profiling: Real-time ML-based correlation and automatic spam categorization.
- Multi-Factor Analysis: Evaluates sender authenticity, frequency, routing, and content.
Flexible Action Framework
- Granular Controls: Block, silently drop, or simulate delivery with fake reports.
- Proxy Monitoring: Transparent pass-through with full logging.
- Monetization Hooks: CDR generation for grey route charging and revenue recovery.
A2P Monetization Enablement
- Traffic Segmentation: Distinguish and legitimize enterprise messaging.
- Partner Onboarding: Enable white-labeling for compliant OTTs.
- Billing Integration: Seamless CDR export to interconnect billing systems.
Analytics & Reporting
- Real-Time Dashboards: Visualize traffic, threat trends, and system performance.
- Revenue Impact Analysis: Quantify recovered revenues and fraud mitigation.
- Compliance Reporting: Support for regulatory audits and consumer protection
Seamless Integration
- Core Network Interfaces: Direct MAP and SMPP integration with MSC, SMSC, and HLR.
- OSS/BSS Connectivity: Open APIs for CRM, billing, mediation, and product catalogs.
- Threat Intelligence Sharing: Integration with global fraud databases.
- Active Directory Support: Centralized user and role-based access management.
How Does Heksagon SMS Firewall Work?
Heksagon SMS Firewall operates as an intelligent filtering layer within your messaging infrastructure, analyzing all MT SMS traffic in real time. The system integrates at the network core, intercepting messages during transit and applying sophisticated detection logic before delivery decisions.
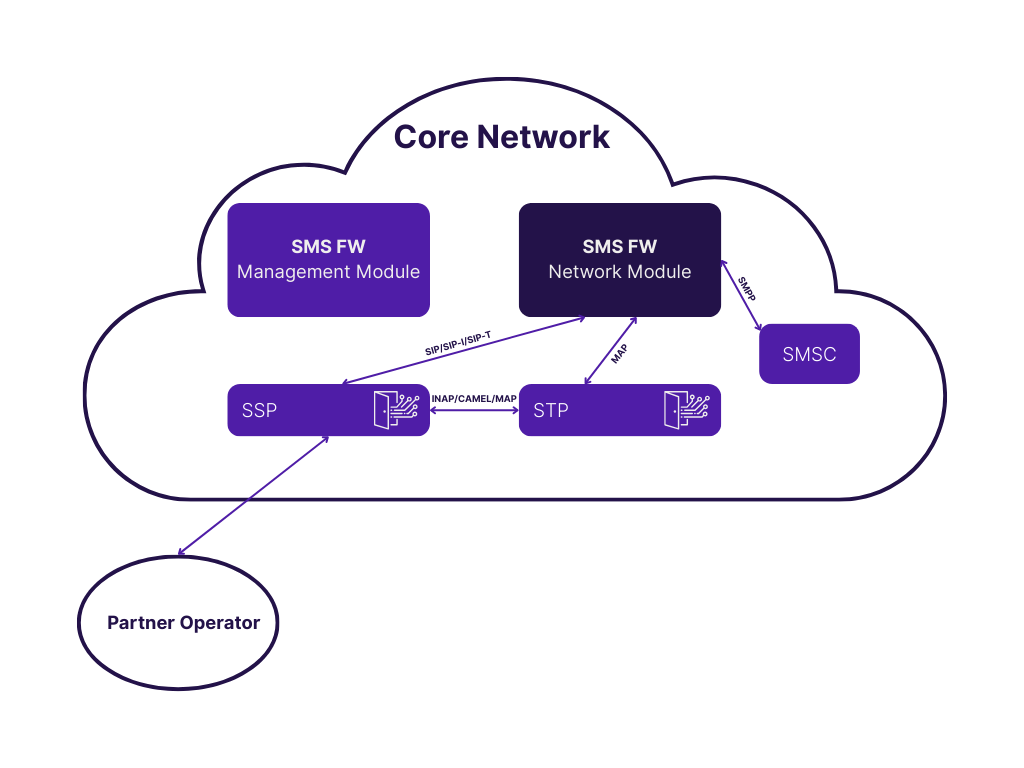
Step 1: Traffic Interception
Messages entering your network through various channels reach the SMS Firewall:
- International Routes
- Domestic Interconnects
- SMPP Connections
- Roaming Partners
- Direct Enterprise Connections
Step 2: Protocol-Level Analysis
The system processes messages at the signaling layer, extracting comprehensive metadata:
Message Reception → Protocol Parsing → Parameter Extraction → Enrichment → Analysis Queue
Extracted data includes:
Source and destination global titles (GT)
- Originating MSISDN or alphanumeric sender ID
- SMSC identification and routing information
- Message content (per SMS segment)
- Submission timestamp and routing path
- Protocol-specific attributes (DCS, PID, UDH)
Step 3: Multi-Layer Detection
Messages are evaluated through cascading detection layers:
- Traffic Classification
- Content Analysis
- Behavioral Analytics
- AI-Powered Risk Scoring
Step 4: Action Execution
Based on detection results and configured policies, the system applies appropriate responses:
- continue (no action)
- reject/block (with custom reason code)
- silently block
- block with fake “message sent” report
- proxy control (transparent pass-through with monitoring and logging)
Step 5: Logging and Reporting
- Comprehensive CDR generation for billing and analysis
- Real-time dashboard updates showing traffic patterns
- Alert generation for security team notification
- Evidence collection for fraud investigation
- Compliance audit trails
Related Products
-
Signaling Firewall
Protect SS7, Diameter, and SIP signaling layers from vulnerabilities and malicious exploits.
-
FinTech Firewall
Help your clients secure financial transactions and voice verification against fraud and unauthorized access.
-
Test Call Generation Service
Continuously validate network integrity and fraud prevention systems with automated test calls.
-
Voice Firewall
Block fraudulent, flash, and spoofed calls in real time, ensuring secure voice traffic and protecting customer trust.
Didn't Find What You Were Looking For?
Frequently Asked Questions
What is an SMS Firewall and why do mobile operators need it?
It’s a real-time messaging security system that monitors and controls all SMS traffic entering operator networks. It scans messages through MAP (SS7) and SMPP interfaces, applying intelligent detection rules to identify fraud before delivery.
What Threats Does Heksagon SMS Firewall Prevent?
By analyzing message content, sender behavior, and routing patterns in real time, Heksagon SMS Firewall addresses these critical threats: Smishing, phishing, and malware, grey route abuse, identity spoofing, SMS flooding, SMS spam, and SIMBOX.
How does SMS Firewall detect grey route A2P traffic?
Grey route detection combines multiple analytical methods: message structure analysis, volume and frequency analysis, sender behavior profiling, SIMBOX fingerprinting, and origination routing analysis. Heksagon’s ML-powered solution correlates these indicators in real time, classifying traffic as legitimate P2P, authorized A2P, or unauthorized grey route with high accuracy.
Can SMS Firewall operate without impacting legitimate messages?
Yes, through sophisticated false positive minimization. Our SMS Firewall employs real-time profiling, whitelisting for authorized enterprise senders, graduated enforcement, and passive monitoring to bring false positives to a minimum. Advanced ML reduces false positives to <0.1% while maintaining 99%+ detection accuracy for actual threats.
What is the difference between active proxy mode and passive monitoring mode?
Active proxy mode integrates SMS Firewall directly into message routing, making real-time delivery decisions. Messages matching fraud scenarios are blocked before reaching subscribers, while legitimate traffic passes through seamlessly. Passive monitoring mode mirrors traffic for analysis without impacting delivery. All messages reach recipients while the system observes, learns patterns, and generates intelligence.
How does SMS Firewall enable A2P monetization?
The platform transforms grey routes from revenue leakage into monetization opportunities through:
- Detection of unauthorized A2P traffic currently bypassing charging systems
- Generation of CDRs for previously unmonetized messages
- Creation of commercial frameworks with enterprise aggregators converting grey traffic to authorized channels
- Implementation of tiered A2P pricing strategies based on message types and delivery guarantees
- Enforcement driving unauthorized traffic sources toward legitimate commercial relationships
Operators typically recover millions annually by combining blocking of non- compliant sources with commercial onboarding of legitimate enterprises previously using grey routes.
Let's Get in Touch!
Interested in our SMS Firewall solution? Fill out the form and our solution experts will contact you in two business days!
