Heksagon Signaling Firewall Solution
Defend your core network against SS7, Diameter, and GTP attacks with comprehensive, real-time signaling security across 2G, 3G, 4G, and 5G networks.

Protect Your Network's Most Critical Asset
Legacy signaling protocols were built for trusted operator environments, not today's threat landscape. SS7, Diameter, and GTP networks face sophisticated attacks daily: location tracking exposing subscriber privacy, call and SMS interception compromising confidential communications, subscriber data harvesting for fraud, roaming fraud generating massive charges, and denial of service overwhelming network elements.
Without signaling protection, your network remains vulnerable to both criminal exploitation and nation-state threats, risking subscriber trust, regulatory compliance, and operational stability. Heksagon Signaling Firewall delivers unified, multi-protocol security protecting your entire infrastructure. Compliant with GSMA FS.11, FS.19, and 3GPP standards, our solution detects and blocks threats in real time while maintaining service quality and interconnect relationships.
Heksagon Signaling Firewall Features
Heksagon Signaling Firewall provides comprehensive protection across all signaling protocols and network generations. Built on carrier-grade architecture with proven deployment experience, the platform combines advanced threat detection, real-time blocking, and intelligent analytics to defend your core network.
Multi-Protocol Security Coverage
- SS7/SIGTRAN Security: Complete MAP, CAMEL, and ISUP protection for 2G/3G networks including location tracking prevention, call interception blocking, and SMS interception defense
- Diameter Protection: Comprehensive security for 4G LTE signaling including S6a, S6d, SLh, and all Diameter interfaces protecting against subscriber fraud, roaming fraud, and DoS attacks
- GTP Security: Tunnel-level protection preventing confidential data disclosure, network overload, and fraud activities across Gn, Gp, and S5/S8 interfaces
- 5G HTTP/2 Security: Next-generation protection for 5G core networks securing service-based architecture (SBA) and API communications
- Cross-Protocol Correlation: Advanced threat detection simultaneously leveraging intelligence across all protocols
Advanced Threat Detection and Prevention
- GSMA Compliance: Pre-configured rules implementing GSMA FS.11 (SS7), FS.19 (Diameter), and 3GPP TS 23.840 security recommendations
- Category 1-3 Threat Protection: Complete coverage of known attack scenarios defined by GSMA Fraud and Security Group
- Stateful Inspection: Deep packet analysis examining message sequences and dialog flows, not just individual messages
- Behavioral Analytics: Pattern recognition identifying anomalous signaling behavior indicating new attack types
- Real-Time Blocking: Immediate message rejection preventing attack completion
Advanced Rule Configuration
- Dynamic Rule Engine: Configurable detection scenarios adapting to network-specific requirements and emerging threats.
- Custom Policy Definition: Operator-defined rules complementing standard GSMA protections.
- Whitelist/Blacklist Management: Trusted partner identification and known threat source blocking.
- Rate Limiting: Signaling traffic throttling preventing DoS attacks and network overload.
- Transparent Testing Mode: Rule validation without impacting live traffic enabling safe deployment.
Network Element Protection
- HLR/HSS Protection: Subscriber data access control preventing unauthorized queries and data harvesting.
- MSC/VLR Security: Call control security blocking unauthorized call routing and interception attempts.
- MME Protection: 4G mobility management security preventing location tracking and unauthorized network access.
- SGSN/GGSN Defense: Packet network security blocking data session hijacking and fraud.
- IMS Security: IP multimedia subsystem protection for VoLTE, VoWiFi, and RCS services.
Roaming and Interconnect Security
- Interconnect Screening: Filtering at network borders accepting only legitimate partner traffic.
- Roaming Fraud Prevention: Detection of SIM box operations, IRSF, and roaming bypass fraud.
- Partner Verification: Authentication ensuring messages originate from claimed sources
- Topology Hiding: Network architecture concealment preventing reconnaissance attacks
- IPsec Support: Encrypted signaling for secure interconnect communications
Intelligent Analytics and Reporting
- Real-Time Dashboards: Live monitoring of threats detected, messages blocked, and security incidents.
- Attack Pattern Analysis: Trending showing attack evolution and emerging threat identification.
- Compliance Reporting: Regulatory documentation demonstrating security due diligence.
- Incident Investigation: Detailed logging enabling forensic analysis and attack source identification
- Alerting and Notifications: SNMP, SMS, and HTTP alerts for critical security events
Flexible Deployment & Ecosystem Integration
- Inline Firewall Mode: Direct integration into signaling paths for real-time blocking
- Monitor Mode: Passive traffic observation for threat intelligence without impacting services.
- Hybrid Deployment: Combination of inline and monitor modes optimizing security and operations.
- Geographic Redundancy: Distributed deployment ensuring business continuity
- Virtual and Cloud Options: NFV and CNF deployments supporting network transformation
Key Threats Prevented
- Location Tracking: Blocks unauthorized SRI queries revealing subscriber locations, protecting privacy and preventing surveillance.
- Call/SMS Interception: Prevents man-in-the-middle attacks intercepting confidential communications.
- Subscriber Data Harvesting: Stops bulk queries extracting IMSI, MSISDN, location, and authentication data.
- Roaming Fraud: Detects SIMBOX operations, bypass fraud, and illegitimate international traffic.
- Denial of Service: Mitigates signalling floods through rate limiting, ensuring network availability.
- Network Reconnaissance: Blocks topology scanning preventing attack preparation.
Integration and Interoperability
- STP Integration: SS7 message routing from Signaling Transfer Points for inspection
- DEA Compatibility: Diameter Edge Agent coordination for unified security architecture
- SEPP Integration: 5G Security Edge Protection Proxy collaboration for next-gen networks
- SIEM Connectivity: Security information and event management system integration
- Northbound APIs: REST interfaces enabling orchestration and automation
How Does Heksagon Signaling Firewall Work?
Heksagon Signaling Firewall operates as a security layer within your signaling infrastructure, analyzing all signaling messages traversing network boundaries in real time. The system examines messages against threat signatures, behavioral patterns, and security policies, immediately blocking malicious traffic while allowing legitimate signaling to pass unimpeded.
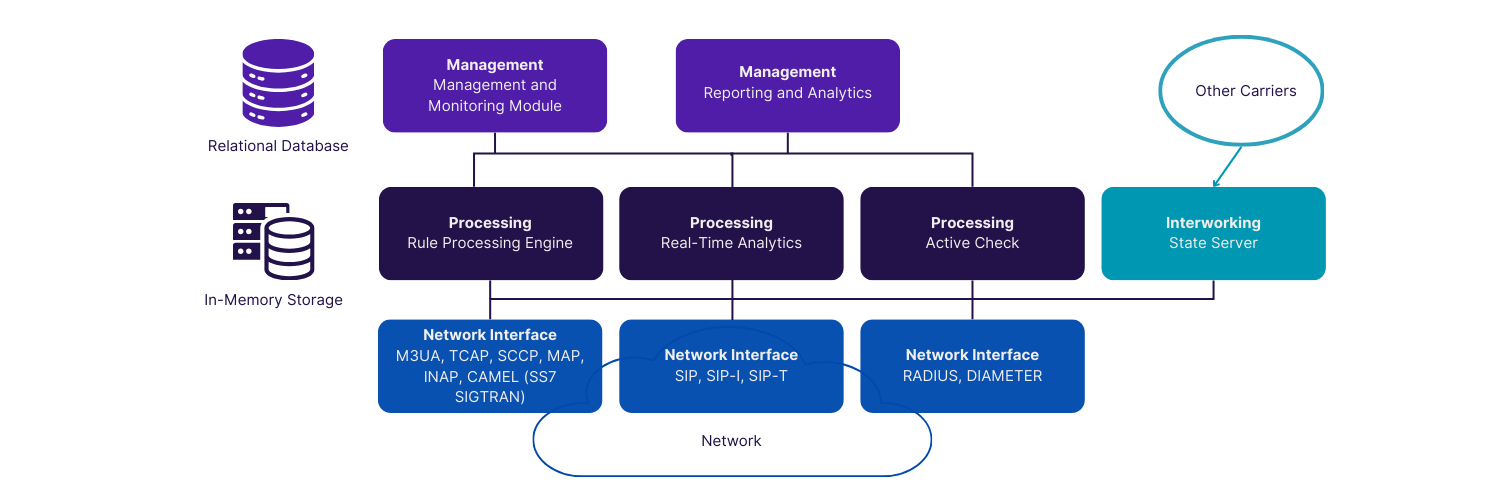
Deep Protocol Inspection & Validation
Every message is analyzed at the structural, semantic, and transactional levels:
- Protocol decoding
- Parameter validation
- Dialog/transaction-aware analysis
- Detection of malformed or suspicious messages
- Compliance checks against GSMA/3GPP profiles
Behavioral & Cross-Protocol Correlation
The firewall correlates signaling events across SS7, Diameter, GTP, and HTTP-2 interfaces to identify:
- Abnormal movement patterns
- Inconsistent location/routing updates
- Impossible call/session sequences
- Multi-step fraud chains
- Silent probing attempts
Decision Engine & Real-Time Enforcement
Once evaluated, each message undergoes real-time decision logic:
- Allow valid traffic
- Block or reject malicious requests
- Trigger alerts or automated workflows
- Log full protocol traces for later analysis
This ensures zero disruption to legitimate subscribers and services.
Related Products
Didn't Find What You Were Looking For?
Frequently Asked Questions
What is a Signaling Firewall and why is it essential?
Signaling Firewall protects core network protocols (SS7, Diameter, GTP, HTTP/2) from attacks exploiting legacy protocol vulnerabilities. GSMA recommends signaling firewalls as essential security infrastructure because networks are vulnerable to location tracking, call/SMS interception, subscriber data theft, fraud, and DoS attacks without protection.
What protocols does the solution protect?
Comprehensive coverage includes SS7/SIGTRAN (2G/3G), Diameter (4G/LTE), GTP (packet networks), and HTTP/2 (5G). Unified platform securing all network generations from legacy 2G through next-generation 5G.
How does transparent testing mode work?
It analyzes all messages and reports what actions WOULD occur but passes all traffic unchanged. It enables rule validation before enforcement, preventing accidental blocking of legitimate partner traffic. As such, it is critical for safe deployment.
What is the Signaling Firewall implementation timeline?
It’s typically 8-12 weeks including integration, configuration, transparent mode testing, and gradual enforcement. The phased approach balances security effectiveness with deployment risk.
How does the Signaling Firewall differ from STP/DEA security features?
While STP/DEA provide basic screening, signaling firewalls deliver stateful inspection, behavioral analysis, threat intelligence, and cross-protocol correlation. Most effective architectures combine both: STP/DEA for basic filtering and signaling firewall for advanced threat detection.
What operational support is required?
It depends on chosen deploying model. Self-managed requires dedicated security team (1-3 FTE). Fully managed service transfers operations to Heksagon experts with 24/7 NOC monitoring. Hybrid models offer a perfect balance of control and expertise, tailored to your business needs.
Let's Get in Touch
Interested in our Signaling Firewall solution? Fill out the form and our solution experts will contact you in two business days!
