Heksagon FinTech Firewall Solution
Secure your client’s mobile money and digital wallet operations with real-time fraud detection, behavioral analytics, and automated response protecting every transaction.

Safeguard Mobile Money Ecosystems Against Sophisticated Fraud
The explosive growth of mobile money globally has created unprecedented fraud opportunities. Account takeover, SIM swap attacks, money laundering, merchant fraud, and identity theft threaten your operations daily, with FinTech companies facing ever-increasing fraud incident cases.
Heksagon FinTech Firewall delivers telecom-grade security engineered specifically for protecting mobile wallet ecosystems. Our solution analyzes every transaction in real time, correlating mobile network data, behavioral patterns, and threat intelligence. By doing so, it effectively detects and blocks fraud before financial impact, protecting your FinTech client’s revenue and customers.
Heksagon FinTech Firewall Features
Fraudsters targeting banks exploit millisecond-fast transactions, coordinate massive bot networks, and leverage social engineering at scale. Heksagon’s FinTech Firewall solution provides MNOs with tools to help enterprise clients gain comprehensive fraud protection. Protect your clients and keep them safe from financial losses, regulatory penalties, and customer trust erosion.
Real-Time Transaction Validation
- Dual-Engine Protection: Transaction API gateway receiving approval requests from mobile wallet platforms, instantly evaluated by real-time rule engine for immediate approve/reject decisions with sub-second latency maintaining seamless user experience.
- Deep Pattern Analysis: Advanced analytical engine processes historical and aggregated data, identifying complex fraud schemes invisible in single transactions. C-language foundation delivers exceptional performance handling millions of transactions daily.
- Multi-Source Data Integration: Unified platform ingesting streaming data (Kafka, RabbitMQ, REST webhooks), file feeds (ASN.1, CSV, archives), telco-specific sources (MSC/IMS xDRs, TAP, GTP), billing data, and mobile money transactions for comprehensive fraud visibility.
AI-Powered Fraud Detection
- Behavioral Analytics: Statistical processing through sliding window analysis, multi-source profiling, cross-stream correlation, and velocity algorithms. Anomaly detection in transaction patterns, geographic behavior, and account usage.
- Machine Learning Models: Purpose-built algorithms optimize detection of money laundering, structured deposits, rapid fund movements, and conversion to untraceable payment methods. Analyzed traffic is used for continuous model refinement.
- Automated Response Framework: Immediate action through direct SMS/email notifications, subscriber barring via billing integration, dynamic blacklist management, triggered KYC verification, case generation for manual review, and external API notifications.
Future-Proof Threat Prevention
- Account Takeover Detection: Location correlation analysis comparing login origins with subscriber locations, access pattern monitoring for unusual timing/frequency, device fingerprint tracking, and simultaneous access detection from multiple locations.
- SIM Swap Protection: Post-activation monitoring tracking authentication attempts, LAC changes, IMEI modifications, contact information changes, behavioral analysis detecting immediate high-risk access, and rapid financial application attempts.
- Identity Verification: Blacklist checks against PANs, subscriber identities, merchants, cross-referenced with government sanctions, stolen card databases, insolvent entity records, and known fraud associations preventing unauthorized access during onboarding and transactions.
- Money Laundering Detection: Structured deposit pattern identification, USSD activity correlation with suspicious transactions, fund movement analysis detecting rapid account-to-account transfers, and conversion tracking to untraceable methods.
Network-Layer Intelligence
- Telco Data Integration: Unique carrier advantage correlating transaction locations with SMS/call origination, device location tracking, impossible travel detection, and VPN usage identification masking true origins, which is visibility unavailable to pure FinTech solutions.
- Geographic Velocity Checks: Real-time correlation of transaction geography with subscriber service usage locations, detection of transactions in locations inconsistent with subscriber profiles, preventing fraud from compromised credentials used remotely.
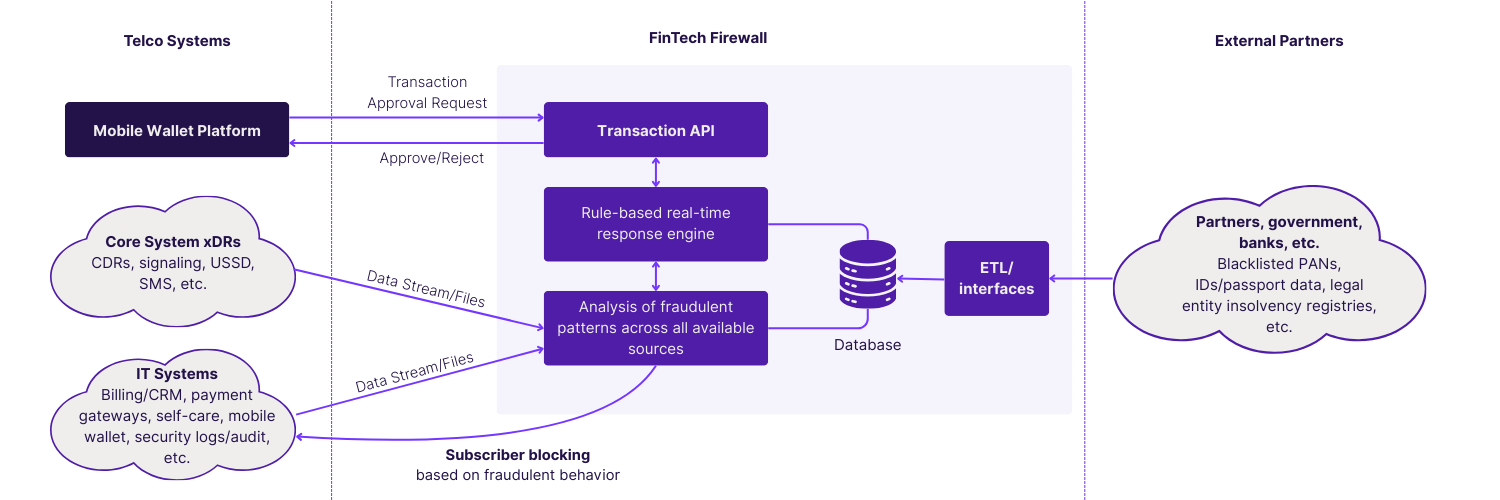
How Heksagon FinTech Firewall Works
Heksagon’s FinTech Firewall acts as your centralized control and analysis hub for the mobile money ecosystem. It delivers complete protection through real-time transaction validation and deep fraudulent pattern analysis. Also, it seamlessly integrates with your client’s core telco systems to secure every mobile wallet transaction and ensure compliance.
High-Performance Architecture
Built on optimized C-language foundation delivering millions of transactions per second with sub-millisecond latency. Horizontal and vertical scaling supporting growth from startup to enterprise volumes while maintaining real-time performance.
Intuitive Operations
Visual pipeline editor for creating and managing data processing workflows, integrated metadata management, self-diagnostic capabilities with real-time KPI monitoring, and performance metrics for individual components enabling rapid troubleshooting and optimization.
Open Platform Economics
Runs on cost-effective open-source infrastructure, compatible with major Linux distributions. Additionally, PostgreSQL database use eliminates expensive proprietary licensing while delivering carrier-grade reliability and security.
Prevent Key Fraud Scenarios
| Prevention Feature | Prevention Methods |
| Blacklist Verification | PAN/payment card checks, subscriber identity validation, merchant verification against sanctions lists and fraud databases. |
| Volume-Based Detection | Transaction threshold monitoring, unusual traffic detection, high-risk merchant category tracking, coordinated activity identification. |
| Velocity Analysis | Geographic impossibility detection, usage pattern correlation, device/location verification, rapid sequential transaction flagging. |
| Money Laundering | Structured deposit patterns, USSD correlation, fund movement analysis, conversion tracking to crypto/untraceable methods. |
| Asset Abuse | Device subsidy exploitation, contract proliferation monitoring, insolvency risk assessment, promotional offer abuse detection. |
| SIM Swap | Post-activation monitoring, behavioral change detection, contact modification tracking, rapid access attempts flagging. |
| Internal Fraud | Manual adjustment monitoring, operator activity profiling, after-hours access detection, override privilege abuse tracking. |
Didn't Find What You Were Looking For?
Frequently Asked Questions
What makes FinTech Firewall different from traditional fraud prevention?
Heksagon’s FinTech Firewall integrates directly with mobile operator networks accessing telco signaling data unavailable to FinTech-only solutions. It correlates transaction data with SMS/call locations, device movements, and network usage patterns, detecting fraud invisible from application layer alone. Additionally, carrier-network integration enables geographic impossibility detection, SIM swap identification, and location-based fraud prevention, all of which are impossible for traditional FinTech security.
How does real-time transaction validation work?
Transactions flow through Transaction API to our real-time rule engine evaluating against predefined fraud indicators with sub-second response. Simultaneously, our analytical engine processes historical patterns detecting complex schemes. Multi-layer analysis includes blacklist verification, velocity checks, behavioral profiling, and cross-source correlation delivering approve/reject decisions instantly maintaining seamless user experience.
What data sources does the solution integrate?
The solution’s comprehensive integration includes streaming data (Kafka, RabbitMQ, webhooks), file feeds (ASN.1, CSV, TAP), telco-specific sources (MSC/IMS xDRs, GTP, billing data), mobile money transactions, government blacklists, bank databases, and regulatory records. Moreover, ETL interfaces enable secure connection with banks, agencies, and external partners fetching blacklisted PANs, identity/passport information, and insolvency records.
Can the system detect money laundering patterns?
Yes, through sophisticated pattern detection analyzing structured deposits (multiple small ATM deposits preceding large transfers), USSD activity correlation (excessive balance inquiries preceding suspicious transactions), rapid fund movement between accounts, and conversion to untraceable payment methods. Behavioral analytics identify layering, integration, and placement phases of money laundering operations.
How does SIM swap detection work?
Post-activation monitoring tracks authentication attempts immediately following SIM activation, LAC changes, IMEI modifications indicating SIM movement to new devices, and contact information modifications. Behavioral analysis detects immediate high-risk service access post-activation, communication pattern changes, and rapid financial application access attempts indicating account takeover via SIM swap.
What operational support is required?
It depends on chosen implementation model. Self-managed requires fraud analyst team (2-4 FTE) managing rules and investigating cases. Fully managed service transfers operations to Heksagon experts with 24/7 monitoring, proactive rule optimization, and incident response. Hybrid models balance operator control with vendor expertise. Visual pipeline editor and intuitive management minimize training requirements regardless of model.
Let's Get in Touch!
Interested in our FinTech Firewall solution? Fill out the form and our solution experts will contact you in two business days!
