Heksagon Interconnect Fraud Management Solution
Interconnect fraud drains MNO revenue by exploiting signaling gaps, routing arrangements, and pricing structures. Heksagon provides real-time detection and instant prevention, ensuring fraudulent traffic is identified and blocked before it impacts your bottom line.

Next-Gen Intelligence for Complete Interconnect Fraud Protection
Interconnect fraud becomes increasingly sophisticated, enabled by complex pricing arrangements, multi-route termination paths, and regulatory diversions. Fraudsters exploit these vulnerabilities to manipulate calling numbers, reroute international traffic through national gateways, or create artificial traffic inflation. Fraud can escalate within minutes, long before CDRs are collected and processed, deeming traditional post-event analysis too slow.
Heksagon solves this by combining near real-time analytics, scenario-driven detection, and in-line call control to stop fraud as it occurs.
Heksagon Interconnect Fraud Management Features
Heksagon integrates analytics, prevention, reporting, and case management into a unified platform designed for real-time, carrier-grade protection.
Usage Data Analytics & Reconciliation
- Robust record validation, filtering, and correlation
- Mediation and standardization of multiple data formats
- Enrichment using CRM, billing, routing, and inventory data
- Technical & commercial traffic analysis (ASR, NER, ACD, margins, revenue/cost)
- Record-level reconciliation with partner-provided datasets for high-accuracy comparison
Real-Time Fraud Prevention
- Inline call screening during setup
- Validation of calling/called/redirecting numbers
- Numeration checks against regulatory and operator ranges
- Prefix, length, and nature-of-address verification
- Blacklist / whitelist enforcement
- Carrier/trunk-level distinctions via service keys
- Scenario-driven actions: continue, release, reroute, or apply duration limits
Fraud Scenario Engine & Pattern Detection
- Caller/called number pattern analysis
- Subscriber and partner traffic profiling
- Volume and time-based anomaly detection
- Trend analysis and statistical deviation detection
- Call correlation and call duration analysis
- Carrier/trunk/product-specific filtering
Typical Fraud Scenario Handling
- SIMBoxes & illegal gateways (profiling + test-call validation)
- External loops / boomerang routing
- Premium-rate / IRSF traffic spikes
- Calling number tampering / origin manipulation
- Suspicious short or long call patterns
- Callback schemes (Wangiri) and DoS/spam attacks
Analytical Reporting & Dashboards
- Near real-time KPI dashboards
- Ad-hoc report builder with drill-down to single CDR
- Threshold alerts (email, SMS, SNMP)
- Report scheduling and multi-format export (CSV/XLS/PDF)
- User- and group-level dashboard sharing
Case Management & CDR Viewer
- Detailed workflow-driven investigation
- Drill-down via CDR/Event viewer
- Automated notifications (email/SMS/SNMP)
- Option to feed confirmed cases into the real-time engine to enforce blocking on future events
Test Call Generator
Supported probes:
- Gateway call probes
- Virtual interconnect probes
- Virtual roaming probes
Detects:
- SIM box & bypass termination
- Calling number manipulation
- False/early answer fraud
- Late release fraud
Additional feature: quality assurance (PESQ-based voice quality metrics).
How Heksagon Interconnect Fraud Management Works
Heksagon’s Fraud Detection and Prevention engine analyzes call signaling at the moment of setup using INAP/CAMEL or SIP interfaces, applying scenario rules and prevention actions in-line. Real-time servers work in load-sharing mode, while analytics and reporting modules process enriched xDR data to deliver actionable insights within minutes. The solution stops fraud before it enters your network, protecting interconnect revenue, preserving QoS, and eliminating the days-long detection delays associated with post-event systems.
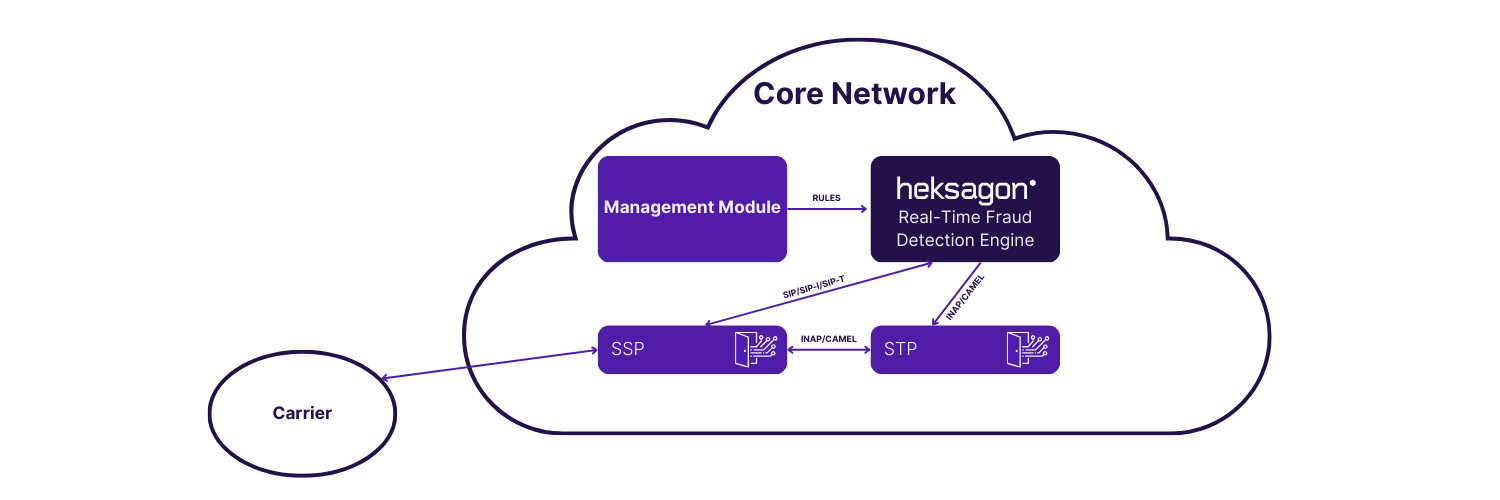
Architecture & Performance
- Load-sharing real-time servers with independent failover capacity
- Multi-homing SIGTRAN/SIP for high redundancy
- Dual-site deployment for geographic resilience
- Horizontal scalability by adding real-time servers
- Optimized processing outside the DB to ensure high throughput and near real-time analytics cycles
Operations & Usability
- Web-based OAM module for rule creation, editing, and activation
- 20-minute operational view showing scenario hits and system load
- User roles with granular privileges
- AD/LDAP authentication support
- Full audit trail of system and user actions, exportable via reporting module
Integration & Compatibility
- SIP, SIP-I, SIP-T
- INAP/CAMEL over SS7/SIGTRAN
- FTP/SFTP, DB-link, SOAP/XML interfaces
- Integration with CRM, mediation, billing, MNP/portability databases, and regulatory numeration sources
Use Cases & Threat Scenarios
- International traffic routed over national interconnects
- National traffic masked as international
- Missing, invalid, or manipulated calling numbers
- SIMBOX and illegal gateway identification
- IRSF, Wangiri, premium-rate pumping
- External loop routing anomalies
- Irregular call duration distributions
- Volume spikes by carrier/trunk/product
Related Products
Didn't Find What You Were Looking For?
Frequently Asked Questions
Which fraud types does Heksagon prevent in real-time?
Heksagon detects SIMboxes, bypass routing, number tampering, IRSF, Wangiri, PBX hacking, external loops, suspicious call-duration patterns, and more using scenario-driven logic and real-time call control.
How does real-time prevention differ from traditional fraud detection?
It evaluates calls during setup using INAP/CAMEL or SIP, allowing the system to block, reroute, or limit calls before they generate losses. Post-event detection cannot prevent revenue leakage.
What protocols does the system support?
SIP/SIP-I/SIP-T, INAP/CAMEL over SIGTRAN, plus SFTP, DB-link, and SOAP/XML for integration with OSS/BSS platforms.
Can new detection rules be deployed quickly?
Yes. The scenario editor enables updates to be activated immediately with no service interruption.
Is the system audit-compliant?
Yes. All user and system actions are logged, stored, and available through audit-specific reporting.
What deployment models are available?
Inline proxy/redirect mode, intelligent network mode (INAP/CAMEL), or monitoring-only mode with support for distributed and multi-site configurations.
Let's Get in Touch
Interested in our SIMBOX Prevention services? Fill out the form and our solution experts will contact you in two business days!
